| This article first appeared in the June 1997 issue of Monitoring Times. |
The Politics of Encryption
It has been well known, although not widely reported until the beginning of this year, that analog cellular telephones are vulnerable to eavesdropping. In the past there were brief public episodes of intercepted phone calls, such as former Virginia governor Douglas Wilder making derogatory statements about political rivals or transcripts of cell phone calls made by members of the Royal family making the rounds in various tabloids, but it wasn’t until this past December that politicians woke up to reality when several of their own were intercepted and recorded by Democratic activists John and Alice Martin in Florida (see the April issue of Monitoring Times for details).
The Cellular Telephone Industry Association (CTIA), a Washington, D.C.-based trade group and self-proclaimed representative of the wireless communications industry, had long downplayed the security weaknesses of analog cellular telephones and had lobbied successfully at the Federal level to make such interceptions unlawful. Their legislative success was ineffective, however, since there was little desire on the part of law enforcement to locate and apprehend violators.
Soon a new story emerged from the industry. Digital systems would save the day and make privacy possible for cellular telephone users. "Electronic stalkers" and other scapegoats would no longer be able to eavesdrop on calls made using these new radio systems. Not only would the digital nature of the new systems protect privacy, but conversations would also be encrypted. Forgotten, apparently, was the fact that the wireless industry had the capability to incorporate encryption into their analog systems, but chose not to. Nonetheless, new encoding techniques had been perfected over the past couple of decades, and military-strength encryption was not only possible, but was being used by thousands of people on the Internet through such software programs as Pretty Good Privacy (PGP). Here was a chance for cellular telephone users to have real security from both the casual eavesdropper and rogue government snoops.
CRYPTOGRAPHY AS MUNITIONS
What is not well known in this country is that cryptographic algorithms, the procedures that describe how to scramble messages, are considered weapons of war and subject to export restrictions under the same arms trafficking laws that control bombs and guided missiles. Responsibility for those laws, termed International Traffic in Arms Regulations (ITAR), was recently transferred from the Department of State to the Department of Commerce, but any cryptographic method that is sufficiently strong to completely protect information is still denied an export permit. Systems that can easily be broken, however, are free from such restrictions. The software program Pretty Good Privacy is strong enough that the author, Phil Zimmermann, was under Federal Grand Jury investigation for violating ITAR by making PGP available on the Internet.
Despite the widespread availability of equally strong, sometimes identical cryptographic systems in other countries, elements of the United States government as well as the Clinton Administration continue to insist that effective, secure systems not be exported. Their stated reason is protection of national security, but the policy has had a chilling effect on computer software and hardware manufacturers, who cannot afford to develop two products, one for export and one for domestic use, and have been forced to produce only the weaker, exportable version. Several bills in Congress this session are designed to loosen ITAR, but similar efforts in past years have been defeated by a coalition of domestic law enforcement and national security agencies.
When the Telecommunications Industry Association (TIA), an independent standards-setting body, set up a subcommittee to develop and propose an industry-wide standard for using encryption in digital cellular systems, they were warned by the National Security Agency (NSA) that if they came up with something that was too effective in protecting cellular voice traffic they would be barred from exporting it. Since few, if any, equipment manufacturers would be willing to develop two products, one for domestic use and one for export, the TIA subcommittee settled on a set of weak algorithms that would pass NSA review. There is still debate as to whether the NSA actually proposed the system or merely approved it, but the end result is that the official, industry-wide encryption standard was seriously weakened ostensibly because of arms regulations.
CELLULAR AUTHENTICATION AND VOICE ENCRYPTION
What the subcommittee finally released, with no public review and stringent ITAR and copyright warnings, is a set of algorithms they termed Cellular Authentication and Voice Encryption (CAVE). As released, CAVE performs three main functions. The first, authentication, assures the cellular system that a phone requesting service is, in fact, a legal subscriber. As described in a previous column (see PCS Front Line, January 1997), older analog systems are vulnerable to fraud from "cloned" phones using stolen ESNs and MINs. The new system issues challenge numbers to phones requesting service, which are transformed using the CAVE algorithm and verified by the mobile switching center (MSC). Due to strong industry interest in reducing high fraud loss rates and a lack of interest from the NSA, this portion of the standard is relatively secure.
The second use of CAVE is to generate a set of code numbers used to protect control channel information, including dialed keypad digits. Any numbers entered on the phone’s keypad are encrypted using the Cellular Message Encryption Algorithm (CMEA) with code numbers from CAVE. This encompasses all telephone numbers, Personal Identification Number (PIN) codes, credit card and other numbers the user may enter.
The third application generates two sets of numbers that are used to "mask" the digitized forward and reverse voice channels. As early as 1992 this method was known to be cryptographically weak and could be compromised with commercially available computing equipment and custom code-breaking software. As one cryptographer has put it, "Any county sheriff with the right PC-based black box will be able to monitor your cellular conversations."
CAVE IS BROKEN
The inevitable finally happened. On March 20th of this year, Counterpane Systems, a consulting company run by cryptographer and author of the popular book Applied Cryptography Bruce Schneier, and University of California at Berkeley graduate student David Wagner announced they had cracked the Cellular Message Encryption Algorithm (CMEA). In their draft report Cryptanalysis of the Cellular Message Encryption Algorithm they revealed several weaknesses and proposed an attack that can be carried out on currently-available computers in a matter of minutes, or at most hours. Using their methods an eavesdropper could easily record all the keypad entries from a targeted cell phone user and crack the messages at some later time.
Rather than calling for stronger encryption or a change in the export regulations, the CTIA downplayed the break and called for yet more laws to make it "illegal to manufacture or modify a device which is designed to perpetrate the illegal interception of PCS calls." What they don't seem to understand is that more laws will not stop eavesdroppers, but strong cryptography will.
PCS FINANCIAL DIFFICULTIES
Things are not going so well for the FCC, either. After issuing press release after press release about how much money their auctions were generating, at the end of March they temporarily suspended the collection of installment payments on broadband PCS licenses auctioned off last year. Under the auction rules, the highest bidder for each license was required to make an initial downpayment of 10 percent and pay the rest in installments over time. Several PCS winners are experiencing financial difficulties and are unable to make payments, and at least one winner, Pocket Communications, Inc., of Washington, D.C., has filed for Chapter 11 bankruptcy. Pocket owes the FCC about $1 billion for their PCS licenses and has additional liabilities of more than half a billion dollars, but has assets of only $1 billion. As more PCS auction winners face the costs of building out their networks and paying for their licenses, the FCC may find it difficult to collect all they expect.
DIGITAL AUDIO RADIO SERVICE
Anyone who has driven long distances and likes to listen to the radio is familiar with the problem of finding a decent radio station in each town they pass. A service that may help alleviate that problem passed another hurdle on April 2 when the FCC completed the auction for two digital audio radio service by satellite (satellite DARS) licenses, raising more than $173 million after 25 rounds. Envisioned as a nationwide, CD-quality audio service, satellite DARS promises to provide a variety of music and news programming for long distance motorists and residents of remote areas.
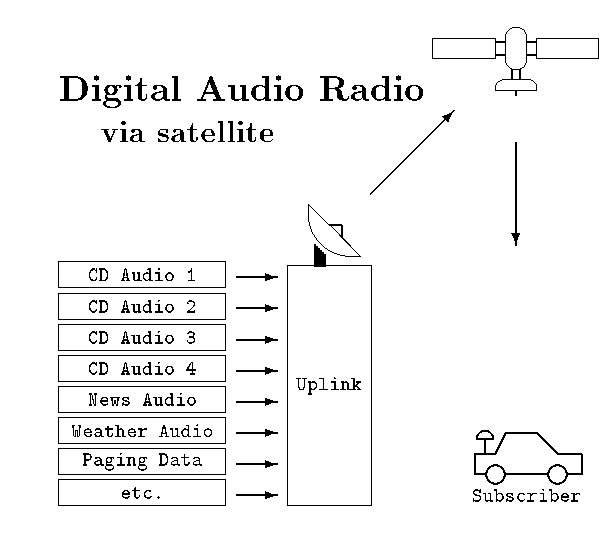
The FCC had originally planned to auction 50 MHz of space between 2310 and 2360 MHz (S-Band) for DARS, but legislation from Congress required the FCC to auction much of that space under what has been termed Wireless Communication Services (WCS). Twenty-five MHz of space remained, and was split into two licenses, EBN001 at 2320 to 2332.5 and EBN002 at 2332.5 to 2345. Each 12.5 MHz-wide license is expected to carry anywhere from 19 to more than 40 digital channels, each of which could carry CD-quality sound, news, emergency information, or even voicemail and alphanumeric paging messages.
Satellite CD Radio, Inc. bid more than $83 million for one license and American Mobile Radio Corporation has promised to pay almost $90 million for the other. The FCC report and order defining the service gives each licensee a year to build their satellites, four years to launch, and six years to put their systems into operation. Each license is good for eight years, and starts from the time the system begins providing service. As has become standard policy, the FCC has declined to specify a particular modulation scheme or channel structure, preferring instead to let private industry develop standards independently. Market forces are expected to drive the two licensees to reach a common format, allowing equipment manufacturers to build consumer equipment that works with either service provider.
| License | Winner | Frequency Range |
| EBN001 | Satellite CD Radio, Inc. | 2320 MHz to 2332.5 MHz |
| EBN002 | American Mobile Radio Corp. | 2332.5 MHz to 2345 MHz |
That's all for this month, and as usual more information is available on the World Wide Web at http://www.grove.net/~dan and I'm reachable via e-mail at dan@decode.com. Until next month, happy monitoring!