| This article first appeared in the January 1997 issue of Monitoring Times. |
Cellular Fraud
With any new technology comes those who would misuse it, and cellular telephones have been no exception. If the Cellular Telephone Industry Association (CTIA) is to be believed, more than $650 million was lost to cellular telephone fraud in 1995, up from $482 million in 1994.
This represents almost four percent of total industry revenues. The CTIA also claims worldwide fraud losses could exceed $1 billion for 1996. Although there is some controversy about how large actual dollar losses are, there is no doubt that fraud is widespread and growing.
There are four common types of cellular fraud currently being perpetrated. From least to most technically sophisticated, they are: phone theft, subscription fraud, tumbling fraud, and cloning.
Theft is simply the stealing of a cellular telephone and using it until the loss is reported. Baltimore, Maryland, police say that cellular phone thefts have risen as high as 22 a day. Most phones appear to be stolen by drug abusers to raise quick cash, but many reach the hands of more sophisticated criminals.
Subscription fraud is the signing up for cellular service using false or stolen identification, with no intention of paying the bill. New subscribers are typically given a one- to three-month grace period before shutting off the account, by which time the criminal could have made thousands of dollars worth of calls. Subscription fraud is not limited to traditional analog cellular. Even Sprint Spectrum, a new digital PCS service covered in the October 1996 column, is working to combat a rising tide of false applications for service.
For the next two types of fraud it is important to understand how calls are placed and authorized in an analog cellular system. For a more complete review, see this column in the December 1996 issue of Monitoring Times.
CALL AUTHORIZATION
Each cellular telephone has an Electronic Serial Number (ESN) hardwired into the phone by the manufacturer. This number is supposed to uniquely and permanently identify each and every cellular phone ever made, and under FCC regulations is never to be changed. Also, when a cellular telephone is put in to service, it is assigned a Mobile Identification Number (MIN) by the cellular service provider. This is the ten-digit area code and telephone number of the phone.
Each cellular telephone also has a "home" system, which is the local area served by their provider. When a call is placed the ESN and MIN, along with other information, is transmitted from the phone on a Reverse Control Channel (RECC) to the Mobile Telephone Switching Office (MTSO) via the closest base station. The MTSO looks up the ESN and MIN in a subscriber database to confirm that the phone is allowed to place a call.
When a cellular telephone is operating outside of its home system, it is said to be "roaming." When a roaming phone places a call, the ESN/MIN pair is still sent, but since the local system does not have a record for the subscriber, it has to make a remote validation request back to the home system. This request does not usually complete in timely manner, so most systems let the first call go through while waiting for a validation response. If the ESN/MIN pair turns out to be invalid, it is placed in a "negative" list and the system will block future calls from that phone.
TUMBLING
Tumbling fraud takes advantage of a weakness in this call validation process by using a different ESN/MIN pair on each call. Specially modified phones "tumble," shifting to a new ESN/MIN pair after each call. These pairs are typically not valid in any system, but made up in such a way as to appear like a legitimate roamer. Occurences of tumbling in major cities has fallen dramatically with the introduction of fast databases and reciprocal validation agreements between cellular operators. Cellular One has helped create a North American Cellular Network (NACN) which provides a standard set of roaming capabilities, including rapid call validation, for customers in several thousand cities.
CLONING
Currently the most lucrative form of fraud for cellular "bandits" is cloning. Using 800 MHz FM signal interception equipment, ESN/MIN pairs are "snarfed" as they are transmitted from the phone to the base station. Since cellular phones also identify themselves when turned on and re-establishing contact, bandits are known to frequent airports, mall parking lots, and bridge overpasses, or anywhere a large number of cellular phones may be in use. In a typical setup, a 800 MHz-capable scanner is tuned to one of the reverse control channels, waiting to capture a mobile data transmission. When a cell phone transmits it's ESN and MIN, the intercepted data stream is passed from the receiver to hardware that extracts the digital ones and zeros that comprise the mobile message. These bits are then assembled by software that reproduces the ESN and MIN.
Certain test equipment may also be used to capture ESN/MIN pairs. Several companies manufacture devices intended for use by service personnel to test and tune phones sent in for repair. These devices are often portable and have the ability to read transmissions from nearby phones.
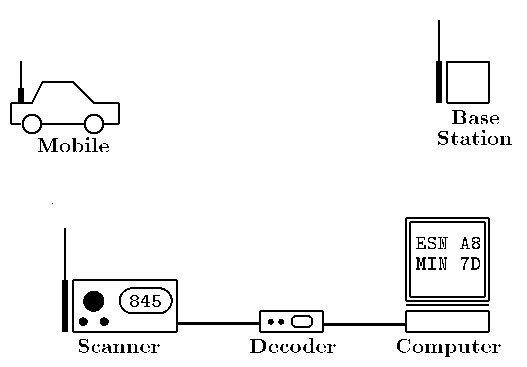
ESN/MIN pairs have also been gathered by computer crackers illicitly entering cellular system databases. In at least one case, however, information from the database was leaked by an employee of the company, and many security analysts caution that the largest risks come from the inside. Some less sophisticated crooks have collected carbon copies and receipts from trash dumpsters in back of businesses that sell cellular phones. This sport, called "dumpster diving," has proven to be surprisingly effective due to the careless disposal of documents by employees.
REPROGRAMMING PHONES
Regardless of the manner in which they were acquired, a cellular bandit uses the active ESN/MIN pair to re-program a second cellular telephone, which becomes a "clone" of the original. Most modern phones allow the MIN to be changed from the keypad, often after entering a special access code. These codes were intended to be released only to authorized service facilities, but are relatively easy to determine from public sources, including technical manuals from the manufacturer. Reprogramming the ESN is a more difficult challenge, but not insurmountable. Early phones had the ESN programmed into industry-standard ROM chips that were easily replaced. Some later phones stored the ESN in non-volatile memory that could be changed using special cables or connectors. Some phones had the firmware that controls the phone also on industry-standard ROMs, which could be later replaced by enterprising individuals. Since a cellular telephone is essentially a radio controlled by a microprocessor, these persons would modify the portions of the phone's software that accessed the ESN, patching to use the pilfered number instead of the one installed at the factory.
FIGHTING FRAUD
Cellular service providers are fielding a number of preventative measures to combat cloning in analog systems.
In many cellular markets today users must enter a Personal Identification Number (PIN) prior to placing a call. Similar to an Automatic Teller Machine (ATM) PIN, the four-digit code is entered after dialing the destination number and pressing SEND. Since this number is sent via DTMF tones (the same touch-tones a landline phone uses) over a reverse voice channel, it will not intercepted by a cloner listening to the reverse control channels. Bell Atlantic Nynex Mobile claimed an 80% reduction in fraud after implementing PINs, and Ameritech Cellular Services reported a 96% drop. This method is vulnerable, however, to a cloner using two scanners and a DTMF decoder. It has also proven to be annoying to many legitimate users.
A common way of detecting cloned phones is the use of customer profiling. A record is kept of the typical calling patterns from a cellular phone, and if any calls are made that stand out from this pattern, the customer is contacted to confirm that the calls were authorized. For example, if a customer typically makes two local calls per day, and suddenly four international calls appear in the span of two hours, a profiling system will notice the discrepancy and alert security personnel.
Some cellular operators offer the simple method of setting limits on dialing capabilities according to customer needs. If a customer will always use the phone within the home system, roaming can be disabled. If the customer will rarely make international calls, the account may be set to demand a PIN prior to placing those calls, but allow all local calls to go through without a PIN.
A more complex, and somewhat successful, method has been introduced in a number of major markets called Radio Frequency (RF) fingerprinting. A "signature" is created and stored for each authorized cellular telephone, consisting of characteristic parameters that uniquely identify the transmitter. The theory is that even between identical cell phones, individual components and tuning variations create enough differences in the transmitted signal that a base station receiver can distinguish one from another. Thus, when a cloned cell phone sends an ESN/MIN pair, the cell system will notice that the transmitted signal doesn't match the signature stored in the subscriber database, and deny the call. This system is not perfect, and trials are continuing to determine the effects of cellular telephone aging and transmission distortion on validation accuracy.
Since the fall of 1995 most new cell phones have been manufactured with the capability of authentication. In this process the cell phone and the base station exchange a "secret handshake" derived from a mathematical algorithm and a 20 digit number. A legal phone identifies itself by transmitting the answer to the algorithm. The keys to this process are stored in the telephone and in the cellular system database, and are never transmitted, so are not vulnerable to interception. This process is also transparent to the user, and requires no additional dialing steps.
Texas Instruments, among others, is working on a voice identification system that allows only previously-recorded users to place calls. At the time of purchase, or soon after, the user records a name or key phrase, which is stored in the cellular system database. Then each time the user wants to place a call, they must speak their name or key phrase and match the stored version to be validated.
This past summer AT&T Wireless Services spent several hundred thousand dollars on an advertising campaign in New York City, one of the major centers for fraud in the United States. Subways, buses, and billboards warned would-be criminals that cellular carriers and law enforcement agencies can track them down. It is not clear how effective the campaign has been.
DIGITAL SYSTEMS
Digital systems provide a greater degree of security against cloning for two main reasons. First, equipment is not currently available to the general public that will decode the more complex signal formats sent by digital cellular telephones. Undoubtedly this situtation will change in the future, but for now such equipment is difficult to obtain. Second is that the air interface will be encrypted by methods that will be very difficult for individuals to decode. Government agencies are maneuvering politically to have encryption strong enough to resist individual decrypting efforts, but weak enough to break using government resources. More on that in a later column.
As usual, send comments, questions, and criticisms to dan@decode.com. Until next month, happy monitoring!